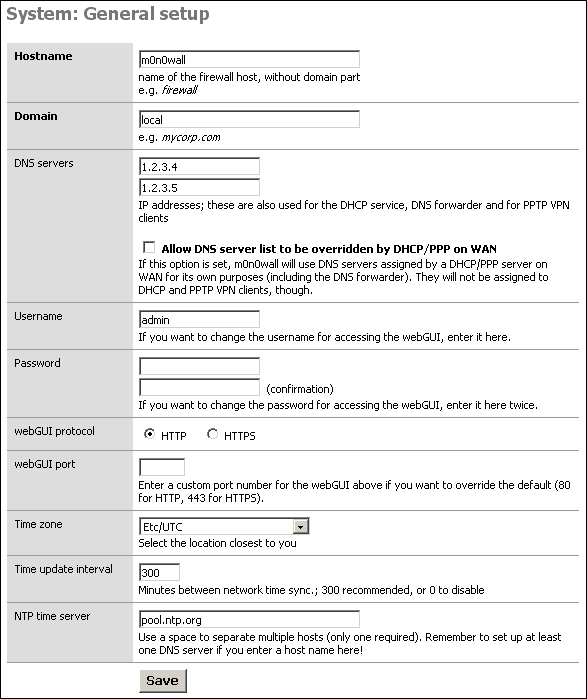
The General Setup screen allows you to control some general parameters of your firewall.
The General Setup screen allows you to change the following parameters:
Table 4.1. General Setup parameters
| Parameter | Description | Example | Reference |
|---|---|---|---|
| Hostname | The unqualified hostname of your firewall. | myfirewall | IP Basics |
| Domain | The domain name to qualify your firewall hostname. | example.com | IP Basics |
| IPv6 Support | A checkbox to enable IPv6 Support in SmallWall. | checkbox | |
| DNS Servers | The IP address of one or more DNS servers for use by the firewall. | 8.8.8.8 | DNS |
| Username | The primary username to use when connecting to the SmallWall web GUI. There can be other users created with limited access, but that is not this user. | admin | |
| Password | The password to use when connecting to the SmallWall web GUI. The current password is not displayed; this field is used only to change the password You should change this when you first install SmallWall. | ||
| webGUI Protocol | The protocol for the SmallWall web GUI to use. If you select HTTPS, you will need to securely access your web GUI using a URL that starts with "https:" and you may enter a signed certificate and key in the Advanced System page. | ||
| webGUI Port | The port for the SmallWall web GUI to use, if not the default. | ||
| Time zone | The time zone of your firewall. This affects the value of times printed to logs. | Logging | |
| Time update interval | How often your firewall should contact the NTP server to update its time. | Logging | |
| NTP time server | The name of the NTP (Network Time Protocol) server(s) for your firewall to use. Multiple servers are supported. | 0.smallwall.pool.ntp.org | Logging |
Static routes are necessary when you have a subnet behind another router on any of your internal networks. Static routes are never required for directly connected networks or if the network in question is reachable through your WAN interface's default gateway.
This is commonly seen in networks with VOIP phones on a separate vlan, routed by the phone server. A static route is created to tell SmallWall that the path to that network is through the phone server.
The Static Routes sub section allow the user to set up static routes in order to reach network that must use a gateway different from the default one. By pressing the + icon, the system allows the user to add new static routes.
The parameters to set up a new route are the following:
Interface: Select the interface to which the route must be applied. This is the interface off of which the destination network is located.
Destination Network: Select the network that have to be reached with Classless Inter-Domain Routing (CIDR) code for subnetting. (see RFC1517, RFC1518, RFC1519, RFC1520 for more details) Summery routes can be used here.
Gateway: The IP address of the router/gateway that the firewall must use in order to reach the defined Destination Network.
Description: Enter an optional description for the inserted route
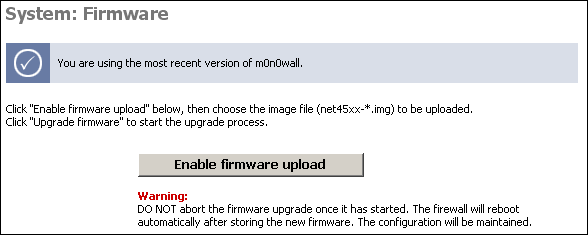
The Firmware screen allows you to upgrade or downgrade your SmallWall version. (not shown on CD-ROM only systems).
The options on the Advanced System page are intended for use by advanced users only. Misconfiguration here can hang the firewall.
Table 4.2. Advanced System Options
| Options | Description |
|---|---|
| Spoof Checking | Spoof Checking blocks packets not sourced from the subnet of the interface the packet was received on. This option only affects bridged interfaces. |
| web GUI SSL certificate/key | Paste a signed certificate in X.509 and a RSA private key in PEM format here. Or generate a new self signed certificate. |
| Firewall Idle Timeout | The time a TCP connection can remain idle before being removed from the state table. The default of 2.5 hours can be shortened here if your state table is filling up. |
| Static Route Filtering | This decides if static route traffic is filtered in the firewall. |
| Firmware version check (Currently disabled) | This will cause SmallWall not to check for newer firmware versions when the System: Firmware page is viewed. (Temporarily unavailable) |
| IPsec Fragmented Packets | This will cause SmallWall to allow fragmented IP packets that are encapsulated in IPsec ESP packets. |
| Outbound NAT Port Range | This setting controls the range from which ports are randomly picked for outbound NAT. Do not change this unless you know exactly what you're doing. |
| Motherboard Monitor | This will display Motherboard information on the system status page for a limited number of supported chipsets. On some systems this may cause a delay in loading the system status page or wrong temperatures. |
| Console menu | This hides the console menu. Changes to this option will take effect after a reboot. |
| IPsec DNS Check Interval | If at least one IPsec tunnel has a host name (instead of an IP address) as the remote gateway, a DNS lookup is performed at the interval specified here, and if the IP address that the host name resolved to has changed, the IPsec tunnel is reconfigured. The default is 60 seconds. |
| Hard Disk Standby Time | This allows the hard drive to power down when idle. As the hard drive is only used when booting of saving a configuration, it can be powered down most of the time. Do not enable this for a flash based drive. |
| Navigation | Keep diagnostics in navigation expanded. |
| webGUI anti-lockout | By default, access to the webGUI on the LAN interface is always permitted, regardless of the user-defined filter rule set. Enable this feature to control webGUI access (make sure to have a filter rule in place that allows you in, or you will lock yourself out!). Hint: the "set LAN IP address" option in the console menu resets this setting as well. |
| IPsec SA preferral | By default, if several SAs match, the newest one is preferred if it's at least 30 seconds old. Select this option to always prefer old SAs over new ones. |
| Device polling | Device polling is a technique that lets the system periodically poll network devices for new data instead of relying on interrupts. This can reduce CPU load and therefore increase throughput, at the expense of a slightly higher forwarding delay (the devices are polled 1000 times per second). Not all NICs support polling. |
| Firewall states displayed | Maximum number of firewall state entries to be displayed on the Diagnostics: Firewall state page. Default is 300. Setting this to a very high value will cause a slowdown when viewing the firewall states page, depending on your system's processing power. |
| Additional Firmware | Load additional kernel modules that will allow using network devices that require a specific firmware module. (Mostly Ralink USB devices) Do not enable any of these modules if all of your network interfaces show up as expected. |
IPv6 support was first included in the 1.3x release. The base for this was actually contributed by Michael Hanselmann way back in 2005, and with some modifications to reflect the changes in SmallWall since then, as well as a few fixes/ improvements.
IPv6 support must be explicitly enabled on the System: General setup page before any of the new options will become available. Also, by default there are no firewall rules for IPv6, so everything is blocked. Make sure to add at least a rule on your LAN interface for outbound connections if you want to use IPv6.
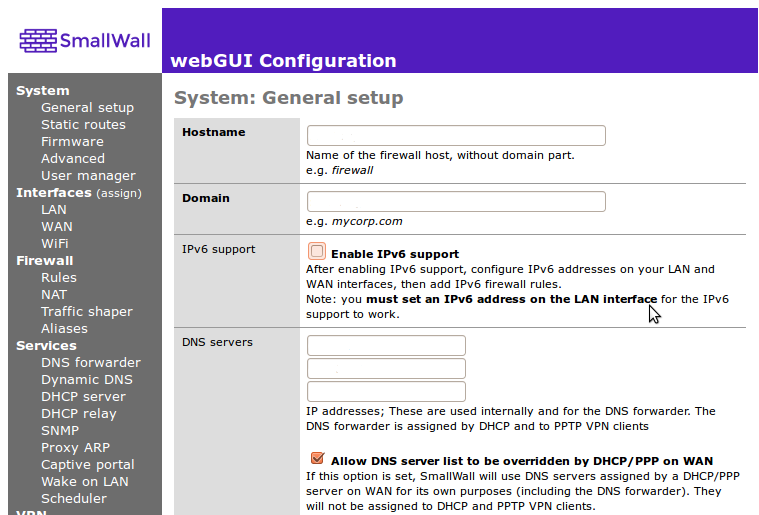
After IPv6 is activated, additional options will become available in the main menu for routing and firewall management. Interface pages will also offer additional IPv6 configuration options. A useful option under the LAN interface will appear to send IPv6 Router Advertisements. This allows other hosts on the LAN to automatically configure their IPv6 address based on the prefix and gateway information that the Firewall provides them.
Caution
While 1.3b12 was the first release with IPv6 support, it has still not been widely used or tested, so bugs in the implementation are likely. (And not just in the firewall) As always, please post on the forum if you've found something odd (with a detailed description of what you did, please). Also let us know if everything worked "out of the box". :)
If you don't have native IPv6 connectivity yet, don't worry: 6to4 tunneling is supported, which should work anywhere you've got a (non- firewalled) public IPv4 address. Simply choose "6to4" for the IPv6 mode on both the WAN and LAN interfaces - no need to manually configure any IPv6 addresses (check the IPv6 RA option on the LAN interface and your LAN hosts will be able to automatically obtain an IPv6 address). It can also work with dynamic WAN IPv4 addresses (LAN/ OPT IPv6 subnets are adjusted automatically). Note that some operating systems do not use IPv6 when connecting to a host that supports both IPv4 and IPv6 if they are configured with a 6to4 IPv6 address (-> RFC 3484), so use an IPv6-only host (try http://ipv6.m0n0.ch) for browser testing, or simply do a "ping6".
If you've got native IPv6 connectivity (over PPPoE/PPTP with 1.3b13 or later), remember that you'll have to statically route your SmallWall's LAN subnet from your upstream router - there's no NAT for IPv6 in SmallWall (and it would be pretty pointless in most cases anyway :).
Also, if you've gotten it to work and need some IPv6 capable web sites to try it out, have a look at http://sixy.ch (or http://ipv6.sixy.ch), a directory of IPv6 enabled web sites.
Note
Although many operating systems support IPv6 by default such as MacOSX 10.4+, Windows Vista and many Linux packages, some systems need it to be activated (such as Windows XP) and some systems may not support it at all (such as the Apple iPhone 2.0 and older versions of Windows). Check your operating system documentation to see if IPv6 is available.
For more information on IPv6 check out some of the following websites.
Additional webGui users can be added here. User permissions are determined by the admin group they are a member of.
Additional webGui admin groups can be added here as well. Each group can be restricted to specific portions of the webGUI. Individually select the desired web pages each group may access. For example, a troubleshooting group could be created which has access only to selected Status and Diagnostics pages.