This tutorial tries to explain how to setup mobile user IPsec VPN with SmallWall and Windows clients that use SafeNet SoftRemoteLT, a popular IPsec VPN client.
Note
This is really not the best way to do this, and it breaks L2TP. Before you go this route, make sure L2TP is not really what you want.
Log into your SmallWall and go to the IPsec: Mobile clients page.
-
Configure the settings as shown in the following picture:
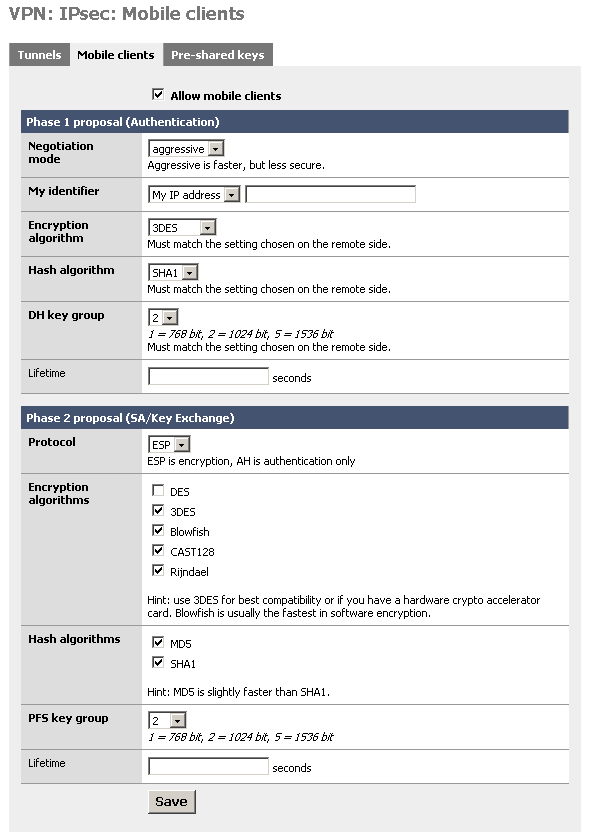
You must use aggressive mode, as only IP addresses can be used as identifiers in main mode.
Note
This makes it incompatible with L2TP.
Click "Save", then go to the IPsec: Pre-shared keys page.
Add a new key for each mobile user (use different keys, and at least 8 characters!). Use the e-mail address of the corresponding user as the identifier.
Go to the IPsec: Tunnels page, check "Enable IPsec" and click "Save".
This example assumes version 10 of SafeNet SoftRemoteLT.
Install SafeNet SoftRemoteLT, if not already installed, and reboot.
Right-click on the SoftRemote icon next to the clock and select "Security Policy Editor".
Choose Edit -> Add -> Connection.
-
Configure the connection properties as follows:
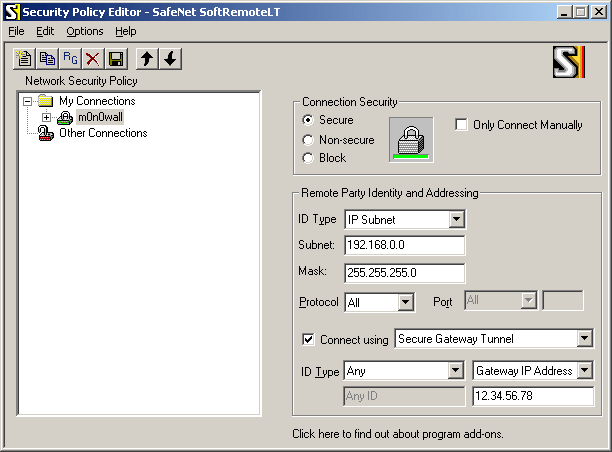
Insert your LAN subnet + mask and enter the external IP address (or hostname) of your SmallWall instead of "12.34.56.78".
-
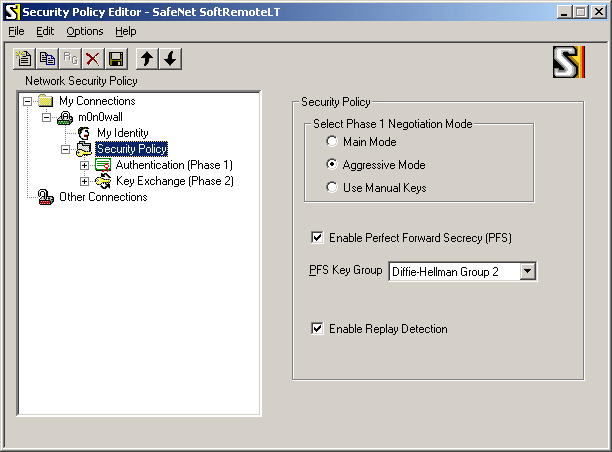
Select "Security Policy" and use the following settings:
-
Select "My Identity" and use the following settings:
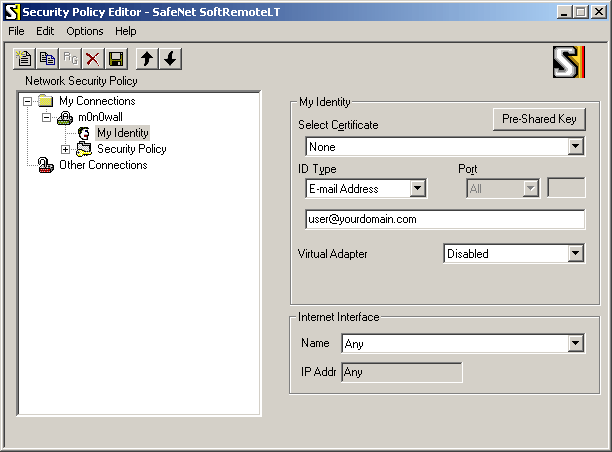
Enter the user's e-mail address, then click the button "Pre-Shared Key" and enter the pre-shared key. The e-mail address (and pre-shared key) must correspond with an entry on the IPsec: Pre-shared keys page on SmallWall.
-
Select "Authentication (Phase 1) -> Proposal 1" and use the following settings:
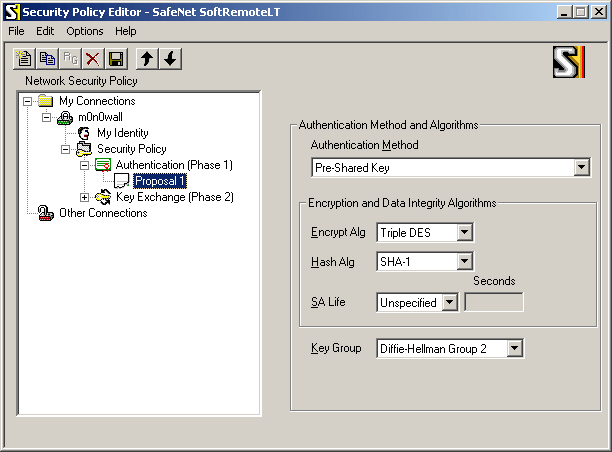
-
Select "Key Exchange (Phase 1) -> Proposal 1" and use the following settings:
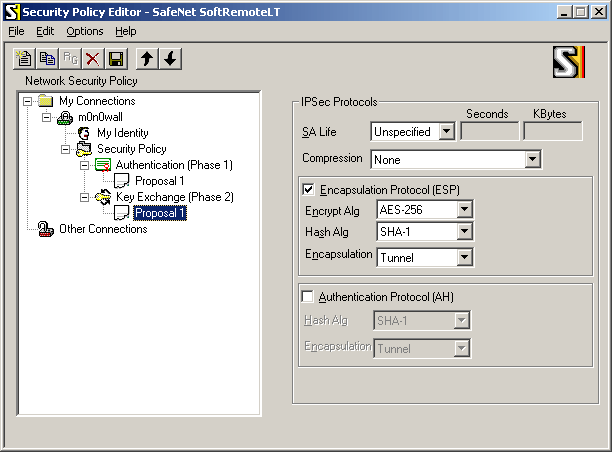
If you have a crypto accelerator card in your SmallWall, you may want to use Triple DES instead of AES-256 as the encryption algorithm (some crypto accelerators do not support AES).
Choose File -> Save.
If you have a crypto accelerator card in your SmallWall, you may want to use Triple DES instead of AES-256 as the encryption algorithm (some crypto accelerators do not support AES).
Choose File -> Save.
Make sure that the Internet connection is established. Try to ping a host on your LAN (e.g. your SmallWall's LAN IP address). The first few pings will time out as it takes a few seconds for the IPsec tunnel to be established. Use SoftRemote's log viewer and connection monitor to tell you what's going on (right-click on the SoftRemote icon next to the clock to open them).